The most prominent method of transmitting secure data in the medical industry is by fax with over...
Don’t get phished.
Email Phishing, SMS, Discord Messages, Skype Messages, we probably heard of at least one incident over the course of the last year that involves phishing for the last ten years. It’s nothing new, and it’s nothing too complicated. So how come it’s still around and why is it still so effective?
—
TLDR:
- Double-check the address the email is from, and make sure it’s the expected sender.
- If you can, do not click links from emails, and instead type in the address yourself. (If it’s an easy address such as “Paypal.me/account” )
- It’s typically disabled by default, however, make sure javascript is disabled on your email client.
—
Phishing is the act of sending a fraudulent message in order to trick the recipient in order to gather information from them. The complexity of a phishing attack will vary on a case-by-case basis. However, the principle behind them is the same: Make a message that seems credible to mask its malicious intent.
One of the common strategies to achieve this, malicious actors tend to impersonate a reputable company. You may have seen cases like these in your own email inbox, where you would see a receipt from amazon or PayPal you don’t recognize. Below is an example of a legitimate PayPal receipt and a phishing receipt.
Left: A legitimate email from PayPal, Sensitive information is redacted.
Right: Fraudulent Phishing Email. (Disabling Javascript can break tags if they have embedded code, however, in this case, they just didn’t provide an image source for their IMG tags resulting in this broken view.)
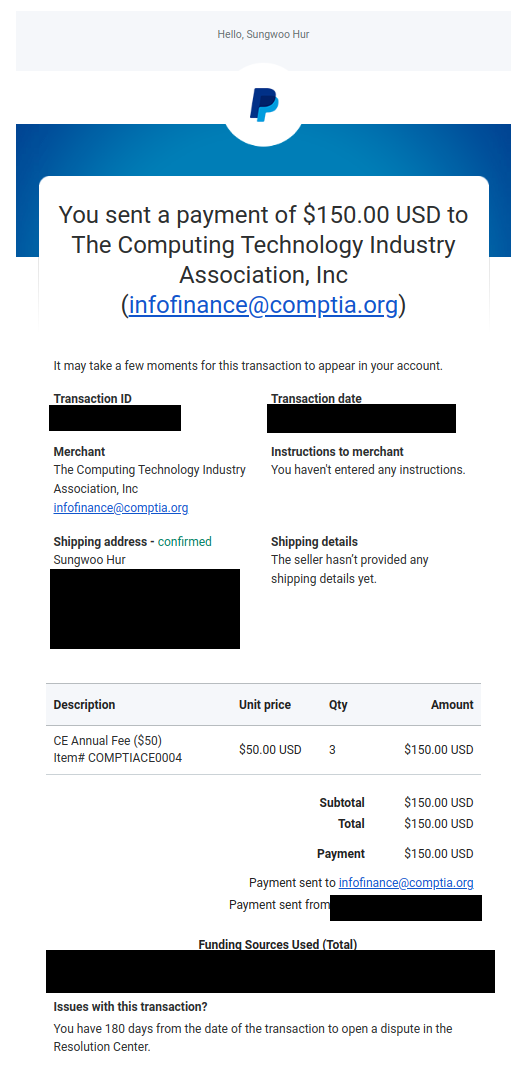
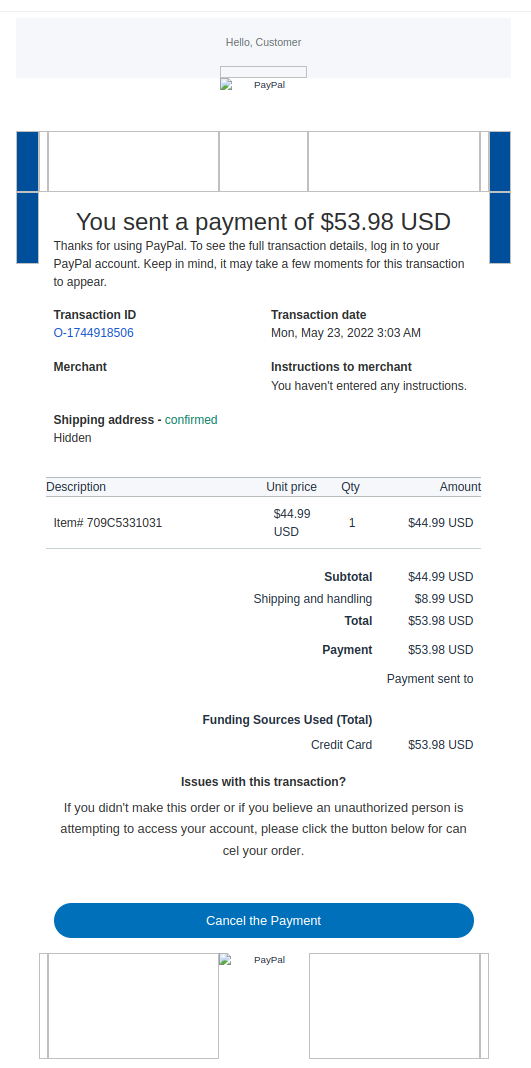
Comparing the two emails, you can see that the information sent, and the format is very similar. Although the right email looks broken if you look at the HTML structure of the two different emails, and how they are set up, these two are actually very similar, the left email also has a table of images as the gradient blue header, it’s just with the right email they do not provide the src URL, resulting in the header looking very broken.
This can indicate they are using an original PayPal email as the template for their fraudulent emails.
The interesting portions start when the emails start to differ:
There are two main points between the emails that are different; the message under the header banner and the call to action for Issues with transactions. Both of these points in the phishing email are more predominantly highlighted, making it an easier experience for the user to understand that if there is an issue with this email, this is the call to action to take. Interestingly enough, having good UX design is a factor in successful phishing scams.
Diving a little bit deeper, I can open up the original message headers sent by both emails and compare the payloads.
Since I am using GMail as the email client I have access to read the DMARC results, which is nice. DMARC is one of the standards that is used for detecting if an email is a scam email or a phishing email on the email client side. In essence, it’s what makes certain emails show up as spam instead of in your inbox.
The technical specifications can be found here: https://dmarc.org/resources/specification/ , and the RFC here: https://datatracker.ietf.org/doc/html/rfc7489 . Or you can look it up as RFC 7489 if you’ve been paying attention to this blog ;).
The overly simplified version of how this all works is:
- Your email server (Gmail in this case) will see if this email has a valid signature by the sender’s domain address
- Gmail will check if this message is sent from an IP address allowed by the domain
- If everything is correct and verified, it will pass the DMARC verification
If you open the email as “View Original” in Gmail, you can see the legitimate PayPal receipt has a long header with the proper signatures, and Gmail shows
SPF: Pass with IP 173.0.84.228
DKIM: ‘Pass’ with domain paypal.com
DMARC: ‘PASS’
Meanwhile, our phishing buddy’s email just has headers
SPF: NONE with IP 0.0.0.0
What this pretty much tells us is that this is not from an email address linked to the paypal.com domain, and not from a server allowed to send emails for paypal.com.
Without prior knowledge about phishing and phishing emails, however, it can be difficult to tell what is a real email and what is not, especially if phishing emails don’t look completely broken like the example used. So what should we look for?
Main things to look for:
Who sent the email?
In most cases, phishing emails will not originate from the actual organization they are impersonating. It will instead come from an address that might be pretending to be from that organization instead. For example, in the case of PayPal, their service emails originate from “service@paypal.com”. However, an impersonator might try to send the email from an email such as “service@paypal.evildoers.com” or “service+paypal@evildoers.com” Be sure to pay attention to the area after the “@” character. If it’s from a legitimate organization it will typically have the root domain (The portion right before the “.com”, “.org” or .”net”) be the organization's domain.
What does the email want you to do?
Phishing emails are usually not informational, they’ll typically want you to click a link or download a file. Most email clients typically do a fair job of sanitizing the email itself, so these are the easiest ways for malicious actors.
So be extra cautious if an email is asking you to do one of those actions.





Blog comments